The QUIC.cloud team is pleased to introduce a collection of Security and Traffic Management Dashboard options available to everyone on the CDN’s Standard Plan. These new options give you more control over your site’s security and crawler traffic.
Let’s start with the new Security options. To follow along, log into your QUIC.cloud Dashboard, select the domain you wish to work with, and navigate to CDN > CDN Config.
Security
There are two new options in the Security section. You can either scroll down until you see them, or you can click Security in the navigation menu.
 Both of these options govern access to your WordPress site’s XML-RPC (RPC stands for Remote Procedure Call), and default to
Both of these options govern access to your WordPress site’s XML-RPC (RPC stands for Remote Procedure Call), and default to OFF.
WordPress XML-RPC support allows your site to receive trackbacks and pingbacks when other sites reference yours, it allows you to publish to your blog from the WordPress mobile app and other remote clients, and it allows the Jetpack plugin to do its thing.
However, XML-RPC also makes your site liable to brute force attacks and DDoS attacks.
If you want to keep XML-RPC for its benefits, then QUIC.cloud can help protect you from its weaknesses. That’s what these two new options are all about.
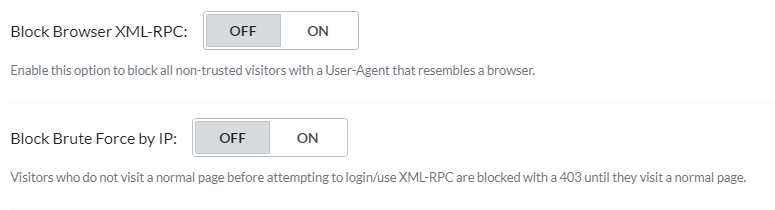
Block Browser XML-RPC
XML-RPC, by design, is a mechanism used by applications to communicate with each other. Browser access is an unexpected method of usage, and likely to be malicious. When this option is enabled, QUIC.cloud will block access to XML-RPC by any non-trusted visitor who appears to be using a browser.
Block Brute Force by IP
This setting provides one way to avoid brute force login attacks. When it’s enabled, QUIC.cloud blocks non-trusted IPs from directly accessing XML-RPC.
The reason for this is similar to the previous setting. Visitors accessing XML-RPC directly is unexpected. However, if the user first visits a normal page on your site, and then hits XML-RPC, that may be a legitimate use. In that case they will not be blocked. Only direct access will be blocked by this setting.
WordPress
Directly under the Security section on the Dashboard is a brand new section called WordPress.
 Through this section, QUIC.cloud addresses the sneaky things attackers may try in order to compromise your WordPress site’s security. All of these options are turned
Through this section, QUIC.cloud addresses the sneaky things attackers may try in order to compromise your WordPress site’s security. All of these options are turned OFF by default.
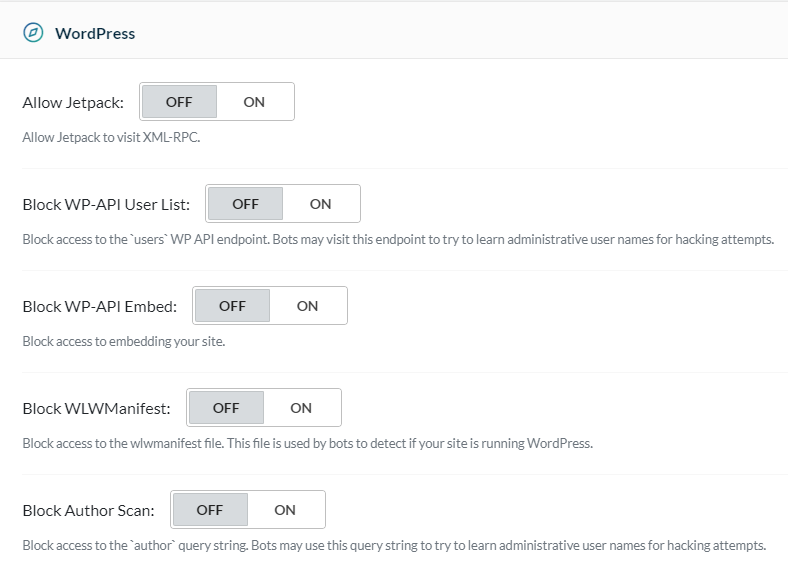
Allow Jetpack
By default, QUIC.cloud does not allow the Jetpack plugin to access XML-RPC. Jetpack, though, is one of the legitimate uses for XML-RPC, so if you want to allow it, you can enable it with this option.
Block WP-API User List
Malicious bots may attempt to access the users WP API endpoint in order to learn administrative user names for hacking purposes. Enable this option to prevent such access.
Block WP-API Embed
When enabled, your site may not be embedded on any other site.
Block WLWManifest
To prevent malicious bots from detecting whether your site is running WordPress, you can enable this option and block access to the wlwmanifest file.
Block Author Scan
Enable this option to block access to author information. This will prevent bots from using the author query string to learn administrative user names for hacking purposes.
Traffic
Once you’re finished with the Security and WordPress sections, you can scroll up to get to the Traffic section. Or you can click Traffic in the navigation menu.
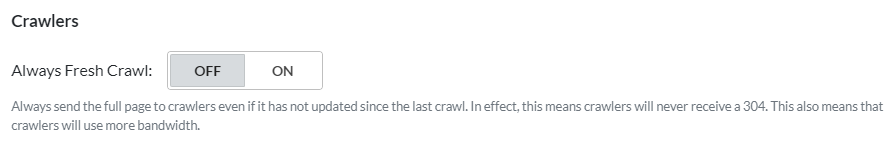 Until now, Traffic Management has been about allowing or blocking site access from certain areas of the world. Now, we’ve added a setting that allows you to manage crawler traffic regardless of origin. Use Always Fresh Crawl to control how much bandwidth you are willing to allow crawlers to consume.
Until now, Traffic Management has been about allowing or blocking site access from certain areas of the world. Now, we’ve added a setting that allows you to manage crawler traffic regardless of origin. Use Always Fresh Crawl to control how much bandwidth you are willing to allow crawlers to consume.
Always Fresh Crawl
QUIC.cloud’s usual behavior is to conserve bandwidth by returning a 304 Not Modified status when a crawler requests content that has not changed since its last visit. This option allows you to change that behavior.
When set to ON, crawlers will always be served the full page, even if the content has not changed since the last crawl. Sending full page content consumes more bandwidth than a simple 304 code. It’s worth noting, though, that bandwidth impact will vary on a site-by-site basis. Small sites with little content may not see much difference at all, while large sites with content-heavy pages could see quite a change.
Conclusion
These new Security and Traffic Management options are here to give you more control. Protect your domains by blocking access to common hacker attack vectors, and take control over the amount of bandwidth consumed by crawler bots.
Tell us what you think. Are you likely to try any of these new settings? Why or why not?